Abstract. The author addresses challenges and threats, their nature, and likelihood of emergence. Information threats are identified in particular and an option for preventing and averting them is proposed.
A review of the events that took place in Russia after the collapse of the Soviet Union reveals good reasons to generalize and analyze the vectors of the country’s movement and development. Historical parallels with the period beginning with the formation of Ancient Rus and up to the formation of the Russian Federation predetermine the importance of such an analysis, since the methods used for its containment (disintegration), although stereotyped, nevertheless remain dangerous and threaten the development and existence of the state.
Challenges and threats that the Russian Federation has faced and can face in the future are divided into military, social, political, economic, and information.1 Let us examine each of them.
Military threats and challenges are more traditional and clear. Hightech weapons and military and specialized hardware systems are used to deal with them. Their use by a potential adversary represents the greatest threat. They include:
• weapons of mass destruction (nuclear, chemical, biological)
• hypersonic cruise missiles and hypersonic warheads of ballistic missiles
• EW assets
• unmanned combat ground-based, aerial, and seaborne vehicles
• combat laser systems
• stealth weapons and military hardware
• global antimissile defense
• weapons based on new physical principles
They are brought together by advanced scientific, technical, and technological projects developed by scientists and Defense-Industrial Complex (DIC) specialists. For example, until relatively recently, due to a lack of specialists and respective materials and technologies, the development of hypersonic weapons in Russia had been halted, but they have now been developed, tested, and are being deployed.
It is very likely that by the 2040s, several countries will possess similar high-tech systems: the US, China, some EU countries, and India. In other countries with influence in the political arena, this work is either at the design and experimental stage or they are buying products from producer countries.
Social threats include changes in society that facilitate a protest movement and change of the constitutional system:
• the steep decline in the standards of living of the population as a result of financial or economic crises
• the coming to power of liberal leaders oriented toward the West and its values
• the creation of tensions between various segments of society and the lack of upward mobility
• unemployment in the age category up to 35-40
In our view, the change of power as a result of a “velvet revolution” is the least probable event. That is why creating tensions between various segments of society and in interfaith and interethnic relations can be expected.
Tensions between various segments of society that emerged after the disintegration of the Soviet Union due to the transition to a new social system and way of life still continue. Income gaps, social insecurity, lack of upward mobility, and low quality of state institutions result in the discontent of a fairly significant part of the population. In the long run, it can become dangerous and be directed at radical measures to change power in the country.
Political threats:
• a change of the political system by radical methods (revolution)
• a pro-Western politician coming to power.
A revolutionary situation in the future, in our view, is unlikely. A pro-Western leader coming to power is unlikely as well. In our opinion, a political crisis could occur if the parties represented in the State Duma and the Federation Council are unable to agree on the further development of the country. It can be generally stated that the political system in Russia is sufficiently stable and capable of countering both external and internal pressure.
Economic threat. The crisis in Ukraine and subsequent accusations of Russia supporting Donbas and annexing the Crimea generated numerous Western sanctions against Russia and certain legal entities and private persons.
The collapse of the ruble against the dollar, bans on Western banks lending to the economy, and restricted access to knowledge-intensive technologies for the industrial sector of the economy resulted in a decline in living standards. However, the measures undertaken focused on import substitution and the manufacture of products on the basis of Russia’s own raw materials, technologies, and hardware components make it possible to speak of the effective neutralization of the expected damage to the development of the economy and society and of prospects of being among the top five economies of the world in the coming decade.
Russia’s economy, having survived the West’s pressure, will continue to develop on the basis of self-reliance, its own raw materials, and production capable of competing in global markets of weapons, food, hydrocarbons, high technologies, etc.
Information threat (ITh). The current century with good reason can be called the information century on account of the rapid development of information technologies as well as the global nature of the Internet. Nowadays, practically any information in any form can be obtained directly at workplaces. Propagation speed and accessibility make it possible to speak about the creation of a virtual space. Our adversaries pay close attention to this space.2 In Western countries, so-called brain trusts serving military and state institutions have existed for decades. According to their estimates, information capable of influencing a person’s consciousness, worldview, and social attitudes is becoming extremely important in this century. It is difficult to overestimate the significance of information threats. They are less cost-intensive and the most efficient in terms of the cost to influence ratio. It is far easier to produce a text, an appeal, a manifesto, and calls for disobedience and protest actions, including unauthorized ones, and post them on social media with an eye to a specific audience than to train agents of influence.
A component of ITh is cyberthreat – the likelihood of unauthorized interference in the functioning of state and military control bodies through the Internet and of influence on economic, financial, and other areas of state activity. Cyberespionage3 is becoming its essential and integral part. Its key tasks involve monitoring electronic storage media and eavesdropping on state, military, and political figures. The use of foreign software (Windows OS) by military and state institutions can be related to threats in the sphere of information technologies.
It should be noted that Russia has always been under implicit or explicit pressure and passed through several historical periods in its development while managing to preserve its statehood, culture, history, and national identity.
At the same time, potential threats capable of playing an important role in the future in the destabilization of the situation in the country cannot be ignored. The information threat, which should be examined more thoroughly, is one of the most important, as was mentioned above.
Information threats are threats where the adversary uses information as a weapon for achieving tactical and strategic objectives in the information space.4 They are covert, intangible, and invisible, which is why they are dangerous. This factor means that they cannot be identified and neutralized in a timely fashion. Destructive attitudes implanted in the consciousness of the target (targets) of aggression can be and most often are long-term, a kind of “land mine in the consciousness” activated in certain circumstances that are advantageous to the adversary. The implementation of such destructive programs could render a serious blow to all areas of vital activity of the state. As far as their nature is concerned, information threats are like an absolute weapon. Significant results in implementing a plan to conquer any state are achieved by altering public consciousness. Western countries have long been coming up with techniques for altering consciousness. As early as the middle of the 20th century, they have been creating such brain centers as the Tavistock Institute of Human Relations, located in the United Kingdom and conducting psychoanalytic research into group and organizational human behavior. Human behavior control studies are its main activity. Developments in this field were successfully applied during psychological and information operations against various countries (Iraq, Libya, Ukraine).
Information technologies make it possible to process a wealth of information in a short period of time, which in turn provides the opportunity to model, assess, plan, and consider with a high probability of implementation practically all potential versions of an event analyzed in the context of tactical or strategic goals and tasks. Consequently, in the near future, the role of humans will be reduced to expanding the database and choosing the best suitable option of achieving the objective from a multitude of potential options. Computing hardware may soon advance to another level. Russian and foreign specialists predict a shift to computing capacities based on new physical principles and a substantial increase in data processing speeds. If that happens, the probability of any predicted event will be close to 100% due to increasing plausible scenarios.
These forecasts mean information countermeasures in various spheres of vital activity are of critical importance. Integration into the global information environment has a flip side. It offers the adversary an opportunity to influence vital state activity virtually – from the information space. This influence is being exerted even now and it will only keep growing in the future.5
Information countermeasures and information warfare are becoming an inseparable part of our life. To effectively control these processes, centralized control must be implemented through the creation of a single information countermeasures system. It can be compared to the country’s air defense system, where a single radar field allows the country to scan the airspace. In our case, it is the global information environment that is being scanned, a single information field is being formed, and a database of threats is accumulated with their subsequent analysis and classification aimed at their early detection and neutralization. A prominent role here is given to artificial intelligence, since humans are not physically capable of reviewing and analyzing the full range of information in real time. In order to neutralize identified insignificant threats, it seems appropriate to develop and introduce specialized programs that exclude human involvement. At the same time, humans are to remain the ultimate decision-makers when it comes to the neutralization of significant tactical and strategic threats. It is natural that in the process of improving methods of information attacks, countermeasures and algorithms will improve as well.
To neutralize information threats, a system of information countermeasures is proposed (Figure) where
• the information environment (IE) is the global information environment consisting of the Internet, mass media, and television in which Russia’s segment is included
• the monitoring center is an IE scanning center for detecting information threats
• the single information processing center is a center for processing IE monitoring results
• the database is a tag repository of potential information threats
• the analysis center is a center analyzing the existence and character of information threats on the basis of obtained sample data
• the decision-making center is a center for making decisions on whether to respond or ignore an information threat and how to neutralize it
• the senior military and political leadership of the country includes high ranking officers and public officials who need to be informed to make a decision when strategic information threats are detected
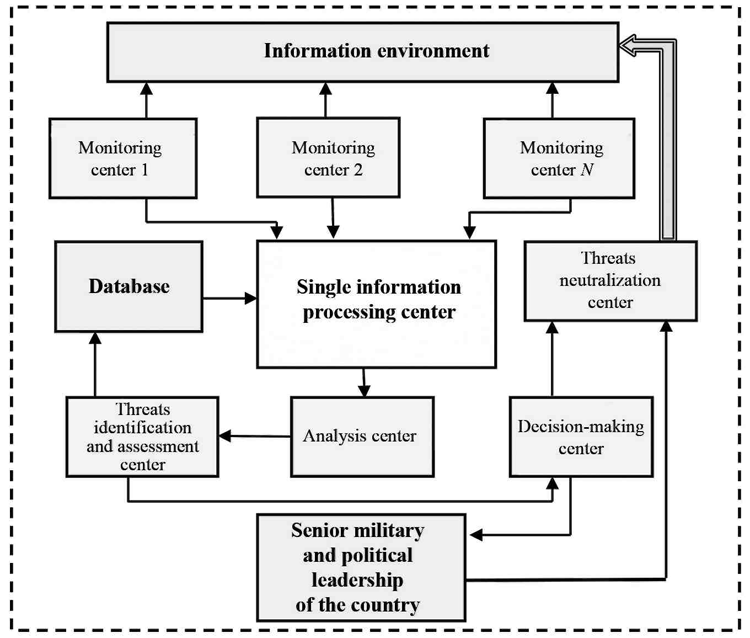
Fig. Information countermeasures system (option)
The action algorithm of such a scheme looks like this: Monitoring centers scan the information environment; if an information threat or attack is detected (localized), data on it are received by the processing center, where primary processing of the obtained data takes place and the “information noise” is removed. The processed information goes to the analysis center, where the nature of the threat is determined. Then the data is sent to the threat identification and assessment center, where they are classified by type and class and according to the main direction of the threat (attack) and the level of danger.
After that, information is sent to the database to be compared with identified threats and their tags are kept there to increase the probability of determining the nature and character of information threats. At this stage, the full identification of the threat is completed. At the next stage, a decision on threat neutralization is elaborated by the respective center. If the threat is critically important, a relevant decision on neutralization is to be made by the senior military or political leadership of the country. If the threat doesn’t exceed acceptable limits or is insignificant, a decision on neutralization is made at the level of the decision-making center. Subsequently, a threat neutralization mechanism is launched in the neutralization center, and the monitoring centers follow the process in order to determine whether the threat has been eliminated and to report to the respective centers.
Integration into the global information environment has a flip side. It offers the adversary an opportunity to influence vital state activity virtually – from the information space. Information countermeasures and information warfare are becoming an inseparable part of our life. To effectively control these processes, centralized control must be implemented through the creation of a single information countermeasures system.
In conclusion, it should be noted that future threats, primarily information ones, make it necessary to search for ways to neutralize them. The proposed option of solving one of the most important problems – the information threat – will make it possible to significantly increase Russia’s defense capabilities.
NOTES:
1. Brusnitsyn, N.A., Informatsionnaya voyna i bezopasnost’ [Information Warfare and Security], Vita-Press Publishers, Moscow, 2001.
2. Panarin, I.N., Informatsionnaya voyna, PR i mirovayapolitika: ucheb. posob. dlya vuzov [Information Warfare, PR, and World Politics: A Training Aid for Universities and Colleges], Goryachaya liniya-Telekom Publishers, Moscow, 2006, p. 62.
3. Brusnitsyn, N.A., Informatsionnaya voyna i bezopasnost’ [Information War and Security].
4. Panarin, I.N., Informatsionnaya voyna, PR i mirovaya politika [Information war, PR and world politics].
5. Ibid.